
This patch removes support in Bitcoin Core for Tor v2 onions, which are already removed from the release of Tor 0.4.6.
- no longer serialize/deserialize and relay Tor v2 addresses
- ignore incoming Tor v2 addresses
- remove Tor v2 addresses from the addrman and peers.dat on node launch
- update generate-seeds.py to ignore Tor v2 addresses
- remove Tor v2 hard-coded seeds
Tested with tor-0.4.6.1-alpha (no v2 support) and 0.4.5.7 (v2 support). With the latest Tor (no v2 support), this removes all the warnings like those reported with current master in #21351
0<bitcoind debug log>
1Socks5() connect to […].onion:8333 failed: general failure
2
3<tor log>
4Invalid hostname [scrubbed]; rejecting
and the addrman no longer has Tor v2 addresses on launching bitcoind.
0$ ./src/bitcoin-cli -addrinfo
1{
2 "addresses_known": {
3 "ipv4": 44483,
4 "ipv6": 8467,
5 "torv2": 0,
6 "torv3": 2296,
7 "i2p": 6,
8 "total": 55252
9 }
10}
After recompiling back to current master and restarting with either of the two Tor versions (0.4.5.7 or 0.4.6.1), -addrinfo initially returns 0 Tor v2 addresses and then begins finding them again.
Ran nodes on this patch over the past week on mainnet/testnet/signet/regtest after building with DEBUG_ADDRMAN.
Verified that this patch bootstraps an onlynet=onion node from the Tor v3 hardcoded fixed seeds on mainnet and testnet and connects to blocks and v3 onion peers: rm ~/.bitcoin/testnet3/peers.dat ; ./src/bitcoind -testnet -dnsseed=0 -onlynet=onion
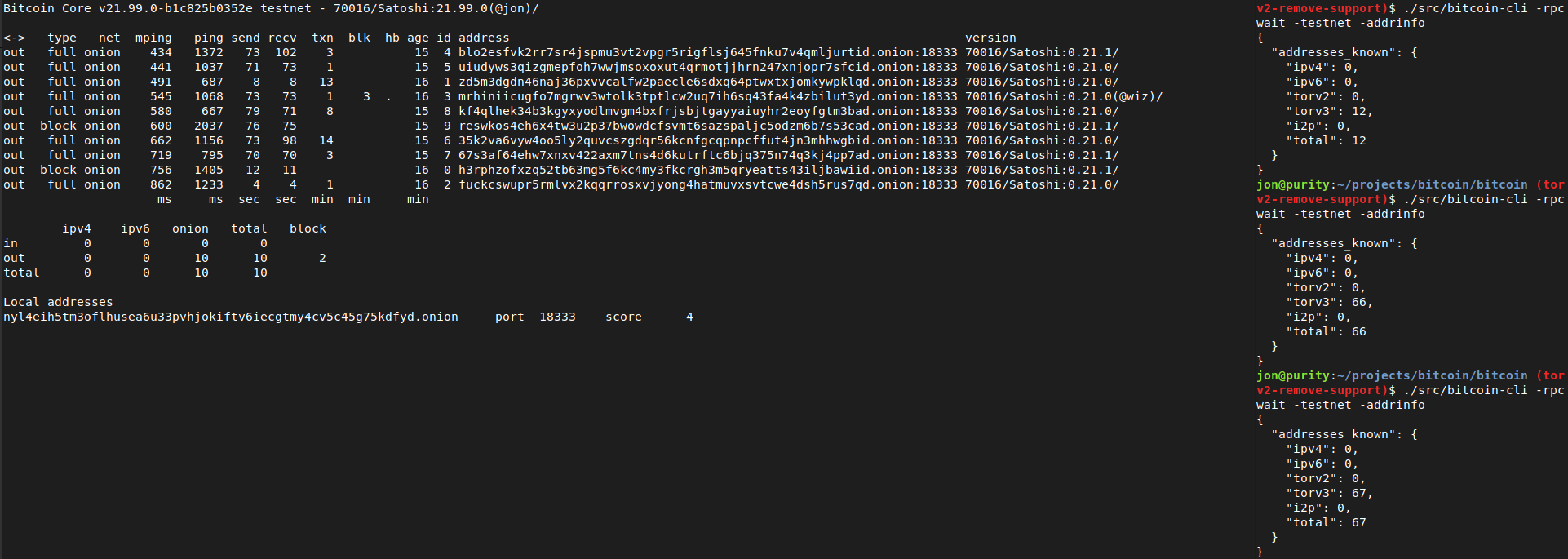
Tested using addnode, getaddednodeinfo,addpeeraddress, disconnectnode and -addrinfo that a currently valid, connectable Tor v2 peer can no longer be added:

Thanks to Vasil Dimov, Carl Dong, and Wladimir J. van der Laan for their work on BIP155 and Tor v3 that got us here.