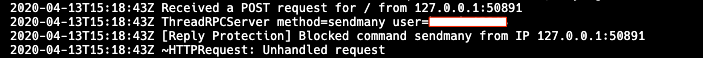
I noticed pull request 128 to python-bitcoinlib where an RPC client retry wrapper is proposed. The retry wrapper would retry in the event of an IOError exception. However, this does not seem particularly safe for RPC calls like sendmany because it could be possible to experience a socket or connection timeout even though bitcoind satisfied the original RPC request. In some cases, auto retrying could result in duplicate spending.
RPC requests should have at least a nonce in every request. It should maybe be a nonce and sequence pair, per @gmaxwell’s suggestion in below chat logs. It would be good to have RPC request replay protection in bitcoind.
Concurrent writes should require locks. Applications should have some sense of guarantees around isolation of competing concurrent and also replayed RPC calls. It’s not enough to “check state” over RPC with listtransactions because you can check state as much as you like, the state still might change between the time you check state and the time you resend the original RPC command, especially in distributed systems.
https://botbot.me/freenode/bitcoin-core-dev/2016-11-21/?msg=76819688&page=2